Table of Contents
A detailed guide on integrating Zero Trust Architecture (ZTA) principles into modern DevOps pipelines.
Keeping DevOps pipelines secure is more important than ever, especially as cyber threats become more sophisticated. A new approach called Zero Trust Architecture (ZTA) is gaining attention as a way to enhance the safety of software delivery. The core idea of ZTA is simple: never trust anyone or anything by default, and always verify before allowing access. This approach helps tackle vulnerabilities that traditional security measures often miss.
DevOps pipelines are increasingly at risk from various threats, such as supply chain attacks, where hackers target software dependencies, and insider threats, where unauthorized individuals can disrupt operations. The interconnected nature of our modern technology makes these risks even more significant. ZTA addresses these challenges by enforcing strict rules about who can access what, continuously checking identities, and closely monitoring activities to ensure that any entity in the pipeline is legitimate before being granted access.
Incorporating ZTA into DevOps processes not only boosts security but also fits well with the need for flexibility and scalability in modern development. By weaving security into the foundation of DevOps workflows, organizations can protect sensitive data, comply with regulations, and lower the chances of breaches. This article will discuss the key ideas behind Zero Trust Architecture, how they can be applied to DevOps pipelines, and the strategies needed to build a secure and resilient software delivery system.
What is Zero Trust Architecture?
Zero Trust Architecture (ZTA) is a fundamental shift in cybersecurity, designed for the complexities of today’s digital landscape. It is built on three core principles: explicit verification of identity and access, enforcement of least privilege access, and assumption of breach. These principles require thorough authentication and contextual authorization for every access request, whether from users, applications, or devices. Unlike traditional perimeter-based security models, which assume trust within the network, ZTA recognizes that threats can arise from both inside and outside, necessitating robust controls at all levels.
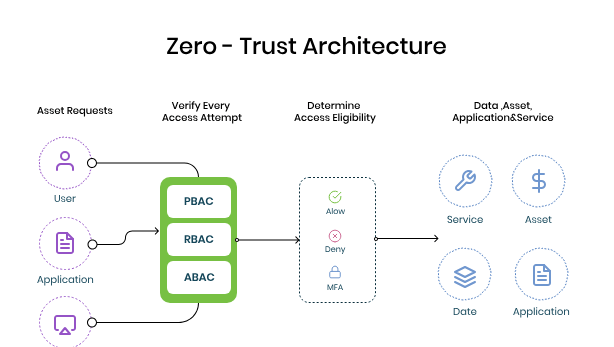
ZTA addresses the shortcomings of the conventional "castle and moat" model, which has become ineffective in light of cloud computing, mobile workforces, and advanced cyber threats. Originally popularized by Forrester Research and formalized by NIST, ZTA mandates continuous verification, eliminating implicit trust.
In modern DevOps environments, traditional security approaches struggle due to the deployment of applications across hybrid clouds and reliance on interconnected tools. ZTA enhances security by implementing detailed policies at every access point, critical for safeguarding the rapid workflows inherent to DevOps.
For organizations utilizing DevOps pipelines, integrating ZTA is essential. The automation and dynamic environments heighten vulnerabilities to unauthorized access, supply chain attacks, and data breaches. By embedding ZTA principles within these workflows, organizations can protect sensitive assets while maintaining the agility needed for rapid software delivery, ensuring secure interactions throughout the pipeline.
Key Components of Zero Trust Architecture in DevOps Pipelines
As organizations embrace DevOps for faster software delivery, security remains critical. Traditional perimeter-based security models, which assume internal network trust, are inadequate in modern cloud-native environments where threats can arise from various sources.
Zero Trust Architecture (ZTA) addresses these challenges by enforcing strict identity verification, continuous monitoring, and least privilege access, ensuring no user or system is inherently trusted.
In DevOps pipelines, implementing Zero Trust principles secures every stage of development and deployment. By incorporating identity management, micro-segmentation, and real-time monitoring, organizations can effectively reduce risks of unauthorized access, insider threats, and lateral movements by attackers. The following components are essential to establishing a Zero Trust framework in DevOps, each crucial for enhancing the pipeline’s security against evolving threats.
Component | Purpose | Security Benefits |
Identity and Access Management (IAM) | Enforce strict access controls based on identity verification and roles. | Reduces unauthorized access and ensures only verified users can access resources. |
Multi-Factor Authentication (MFA) | Requires multiple forms of verification for accessing resources. | Mitigates the risk of credential theft and strengthens access security. |
Role-Based & Attribute-Based Access Control (RBAC & ABAC) | Assigns access permissions based on roles and attributes. | Enforces the principle of least privilege, reducing insider threats. |
Micro-Segmentation | Isolates different environments and segments within the DevOps pipeline. | Prevents lateral movement of threats, reducing the attack surface. |
Dynamic Policy Enforcement | Adapts security policies based on the current context and environment. | Ensures that only approved data flows and actions are permitted within segments. |
Zero Trust Network Access (ZTNA) | Controls user access to resources based on identity and context. | Tightly controls access, ensuring users can only interact with authorized resources. |
Continuous Monitoring & SIEM | Monitors the pipeline for security events and anomalies in real-time. | Enhances threat detection capabilities, allowing for prompt response to incidents. |
Machine Learning for Anomaly Detection | Analyzes patterns to detect deviations that may indicate threats. | Improves the accuracy of threat detection and reduces false positives. |
Automated Incident Response | Automatically remediates identified threats. | Reduces the time to respond to and mitigate security incidents, minimizing damage. |
Traditional Security vs. Zero Trust in DevOps Pipelines
Traditional security models have mainly focused on perimeter defenses, operating under the assumption that threats only come from outside the network. This grants implicit trust to internal users and devices, making systems vulnerable to insider threats, lateral attacker movement, and misconfigurations. Additionally, periodic monitoring and reactive incident response often delay threat detection and increase breach risks.
Zero Trust Architecture (ZTA) disrupts this approach by eliminating implicit trust and enforcing continuous verification throughout the DevOps pipeline. ZTA posits that threats can arise from anywhere, including within the organization. It employs fine-grained access controls, adaptive authentication, and real-time monitoring to protect every interaction. The table below illustrates the key differences between traditional security measures and Zero Trust Architecture in DevOps environments.
Aspect | Traditional Security Approach | Zero Trust Architecture (ZTA) |
Perimeter-Based Security | Relies on strong perimeter defenses (e.g., firewalls) to protect resources inside. | Assumes breach, enforces security at every layer, not just the perimeter. |
Access Control | Broad access control often based on network location or static rules. | Granular, identity-based access control with dynamic policy enforcement. |
Trust Model | Implicit trust for users inside the network perimeter. | Zero implicit trust; every request is authenticated, authorized, and encrypted. |
Lateral Movement | Limited visibility and controls over lateral movement within the network. | Micro-segmentation and continuous monitoring to prevent and detect lateral movement. |
Authentication | Single-factor authentication (e.g., username/password) is often sufficient. | Multi-factor authentication (MFA) is mandatory for all access attempts. |
Resource Access | Users often have more access than necessary (overprivileged accounts). | Access is granted on a need-to-know basis, following the principle of least privilege. |
Security Monitoring | Periodic or reactive monitoring, with limited real-time capabilities. | Continuous, real-time monitoring with advanced threat detection and analytics. |
Incident Response | Manual, slow, and reactive incident response. | Automated, proactive incident response with real-time threat remediation. |
Compliance and Auditability | Challenging to maintain consistent policies and audit trails. | Enhanced compliance through continuous policy enforcement and detailed audit logs. |
Implementing Zero Trust in DevOps Pipelines
Implementing Zero Trust Architecture (ZTA) within DevOps pipelines necessitates the infusion of security at every phase of the development lifecycle, emphasizing continuous verification and stringent access controls for sensitive resources. This paradigm empowers organizations to fortify their development workflows against both internal and external threats while retaining the necessary agility that DevOps practices promote. Below are the critical steps for embedding ZTA principles into contemporary DevOps pipelines:
Establishing Identity and Access Management (IAM)
Effective identity and access management (IAM) is crucial to Zero Trust Architecture (ZTA). Advanced identity verification mechanisms ensure that both users and machines are authenticated before accessing resources. Role-Based Access Control (RBAC) allows for granular permissions, providing users and applications with only the necessary access. Just-in-time access policies further minimize risks associated with prolonged access to sensitive systems.
ZTA centers around access control and identity verification, positioning identity as the new perimeter. This shifts the focus from network security to protecting data and services based on user and device identity. Strategies include Attribute-Based Access Control (ABAC) and Multi-Factor Authentication (MFA), which require multiple verification factors such as passwords, security tokens, or biometrics. By integrating strong identity verification and precise access controls, ZTA significantly lowers the risk of unauthorized access and potential credential compromise.Securing the DevOps Toolchain
The DevOps toolchain, encompassing CI/CD platforms, source control systems such as GitHub, and artifact repositories, presents a significant attack surface for cyber threats. To bolster security, it’s essential to implement multi-factor authentication (MFA) and single sign-on (SSO) to enhance identity verification processes. Continuous monitoring of access policies is crucial, necessitating ongoing adjustments to user privileges based on role changes or detected anomalies. Additionally, configuring encryption protocols for both data-in-transit and data-at-rest is critical to safeguarding sensitive resources within the toolchain.Continuous Monitoring and Threat Detection
To implement Zero Trust Architecture (ZTA), organizations must establish real-time monitoring across all pipeline activities using Security Information and Event Management (SIEM) platforms or cloud-native security tools for swift threat detection and response. By analyzing activity logs, organizations can identify anomalies, manage risks, and maintain compliance.
A key aspect of ZTA is continuous monitoring, which rigorously assesses network activities and access requests for potential threats, moving beyond traditional reliance on human reviews. Utilizing advanced technologies like artificial intelligence (AI) and machine learning (ML), this approach enables rapid anomaly detection through the analysis of data from system logs, network traffic, and user behaviors.
Incorporating continuous monitoring into the DevOps pipeline allows organizations to assess security posture regarding deployments, configurations, and code integrity. Automating vulnerability checks and alerting teams to suspicious activities significantly reduces the time needed to identify and remediate security incidents.
These strategies collectively create a resilient, secure DevOps ecosystem built on the principles of Zero Trust.
Practical Considerations for Adopting Zero Trust
Implementing Zero Trust Architecture (ZTA) within existing DevOps pipelines represents a significant shift that can be both transformative and challenging. Organizations often encounter resistance stemming from the perceived complexity of ZTA and concerns regarding potential disruptions to productivity. Additionally, legacy systems and workflows that are not inherently aligned with ZTA principles can exacerbate the difficulties of integration.
To successfully navigate these challenges, a methodical approach is essential. This approach should emphasize a phased integration strategy that allows for incremental adoption of ZTA principles. Effective communication and robust collaboration among cross-functional teams are critical to facilitating this transition.
While DevOps offers substantial benefits in terms of speed, efficiency, and collaboration, it also introduces unique security challenges. The rapid development cycles and diverse range of tools and technologies can lead to security being sidelined. This discussion will delve into the primary security vulnerabilities associated with DevOps practices, as well as the limitations of conventional security strategies in addressing these emerging concerns.
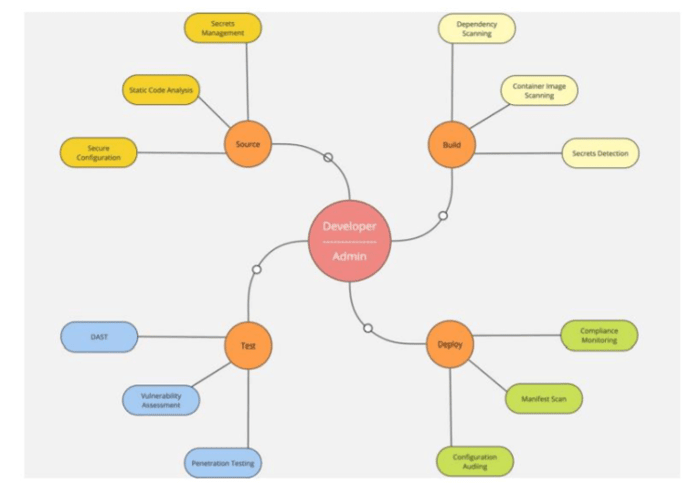
Balancing security with productivity is paramount for the effective adoption of Zero Trust Architecture (ZTA) within DevOps workflows. Developers thrive in agile environments, and imposing overly stringent security protocols can stifle innovation and efficiency. To achieve this balance, organizations should integrate security practices directly into their CI/CD pipelines, employing automated security checks and context-aware access controls. This approach ensures that security is woven seamlessly into development processes, enhancing protection without impeding speed.
Case studies from industry leaders like Google and Capital One illustrate the practical implementation of ZTA in DevOps. Google's BeyondCorp model exemplifies continuous authentication and access control based on the specific context of the user and device, thereby removing the assumption of implicit trust. Meanwhile, Capital One has successfully embedded ZTA principles into its cloud-based development workflows, safeguarding its pipeline while facilitating rapid deployment cycles.
These examples underscore that with thoughtful planning and the right set of tools, ZTA can effectively secure DevOps environments against contemporary threats without sacrificing the agility that is essential for modern software development.
By methodically addressing potential challenges, leveraging established best practices, and drawing insights from real-world implementations, organizations can transition to a Zero Trust framework that enhances the security of their DevOps ecosystems while preserving productivity and scalability.
Conclusion
Zero Trust Architecture (ZTA) reshapes security for modern DevOps pipelines by addressing sophisticated threats like supply chain attacks and insider risks. Its core principles—explicit verification, least privilege access, and the assumption of breach—create a resilient framework that secures every phase of the software delivery lifecycle.
ZTA provides enhanced visibility, robust access controls, and continuous monitoring, significantly reducing vulnerabilities in dynamic environments. Differing from traditional perimeter-based security, ZTA adopts a proactive approach that aligns with agile DevOps workflows, safeguarding the toolchain while enabling real-time threat monitoring and secure collaboration.
Organizations can initiate ZTA adoption on a small scale, starting with securing CI/CD tools or implementing role-based access controls, then gradually expanding as familiarity increases. Experts are encouraged to explore Zero Trust methodologies through literature, case studies, and community forums to strengthen their DevOps security posture.
Akava would love to help your organization adapt, evolve and innovate your modernization initiatives. If you’re looking to discuss, strategize or implement any of these processes, reach out to [email protected] and reference this post.