Table of Contents
How to implement Advanced API Security in your development lifecycle.
APIs, or Application Programming Interfaces, play a vital role in contemporary software, enabling functionalities for mobile applications, Internet of Things (IoT) devices, and cloud services. While developers often prioritize rapid feature additions and ease of integration, it’s important to remember that each API call handles sensitive data, which can lead to serious security issues if not properly protected.
Many teams utilize basic security measures such as API keys, HTTPS encryption, and simple rate limits, often underestimating their vulnerabilities. For instance, API keys are susceptible to theft, while TLS encryption secures data in transit but fails to identify malicious content. Additionally, static rate limits can be easily circumvented by determined attackers. These inadequate protections leave APIs open to sophisticated threats, including injection attacks and denial-of-service attacks.
By the end of this article, you will have a plan to enhance your API security, covering methods like mutual TLS, access controls, threat modeling for REST and GraphQL, and real-time defenses with API gateways and anomaly detection. You’ll gain practical tips and tool suggestions to effectively secure your APIs as your business grows.
What Is API Security?
API security involves protecting the integrity, confidentiality, and availability of the data and services provided by your APIs. As essential components of modern applications—ranging from mobile clients and web front ends to IoT devices and microservices—APIs play a vital role in facilitating important business transactions and data flows. Ensuring their security goes beyond just encrypting traffic; it requires a comprehensive approach that encompasses design, development, deployment, and ongoing monitoring.
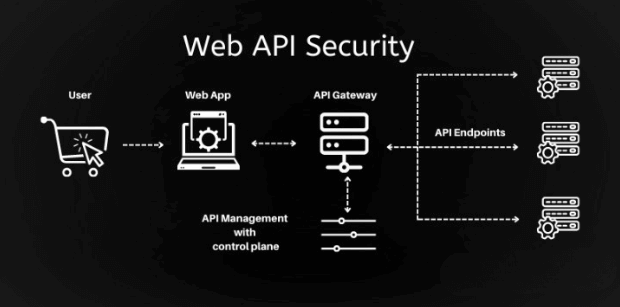
API security encompasses all measures taken to prevent unauthorized access, data leakage, and service disruption. Its primary objectives are to:
Authenticate & Authorize: Verify that every request originates from an approved user or service, and enforce least-privilege access.
Protect Data: Ensure sensitive information remains confidential in transit and at rest.
Maintain Integrity & Availability: Detect tampering, prevent abuse (e.g., DoS), and sustain reliable uptime.
Audit & Comply: Generate detailed logs and reports for forensic analysis and regulatory requirements.
Basic vs. Advanced Security
While foundational controls stop many rudimentary attacks, they fall short against sophisticated adversaries. The table below contrasts core capabilities:
Aspect | Basic Security | Advanced Security |
Authentication | API keysStatic tokens | OAuth 2.0 flowsJWT validation mTLS |
Encryption | TLS/HTTPS only | Payload encryption TLS 1.3 with Perfect Forward Secrecy |
Authorization | IP whitelistingFixed quotas | RBAC/ABAC Context-aware, dynamic throttling |
Monitoring | Server logsBatch reviews | Real-time analytics Anomaly detection Automated alerts |
Threat Modeling | Ad hoc, periodic scans | Continuous STRIDE/OWASP Top 10 integration in CI/CD |
Modern APIs face a rapidly shifting array of attack vectors. Today’s threats include:
Automated Abuse: Botnets executing credential stuffing, API scraping, and volumetric DDoS.
Injection & Payload Attacks: Exploits targeting SQL/NoSQL databases, XML parsers, or GraphQL introspection.
Supply-Chain Vulnerabilities: Compromised third-party SDKs and API dependencies introducing hidden backdoors.
Business-Logic Exploits: Rate-limit bypass, unauthorized fund transfers, or transaction chaining.
Zero-Day & Chained Attacks: Combining low-severity bugs to orchestrate high-impact breaches.
Grasping these fundamental aspects—what API security involves, how advanced controls differ from basic measures, and the focus areas for attackers—prepares you to establish robust defenses that can evolve with your APIs.
Advanced Authentication & Authorization
Enhancing your API's security begins with strong authentication and accurate authorization. Advanced methods not only confirm the identity of the user calling your API but also ensure they can only perform actions they are allowed to. Let’s examine four key patterns that serve as the foundation for a secure access layer.
OAuth 2.0
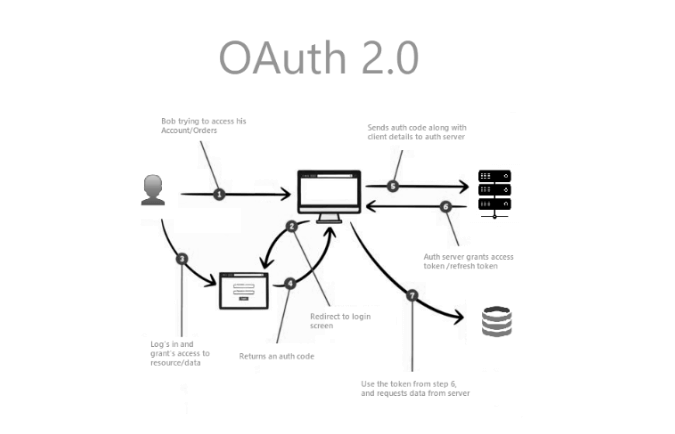
OAuth 2.0 allows delegated access without sharing user credentials, but not all grant types are equal. Select flows that minimize risks and support modern security enhancements.
Authorization Code (with PKCE):
Best for web and mobile apps
PKCE prevents interception of authorization codes
Client Credentials:
Ideal for service-to-service communication
Store client secrets in vaults or HSMs to limit leakage
Refresh Tokens:
Use short-lived access tokens and rotate refresh tokens frequently
Revoke on anomalies (e.g., geo-jumps or token reuse)
Avoid Implicit & Password Grants:
Prone to token leakage and user-credential exposure
JSON Web Tokens (JWT)
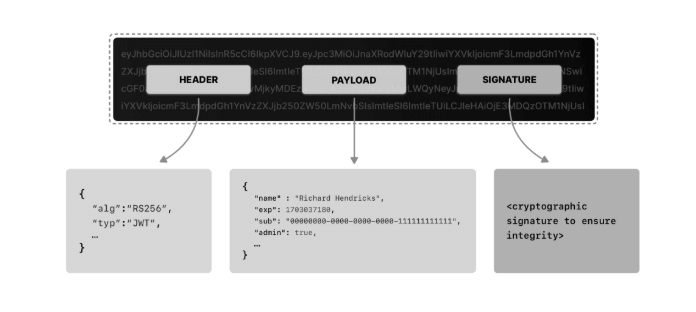
JWTs are compact, URL-safe tokens that carry user claims and permissions in a signed payload. To ensure their integrity:
Sign with Asymmetric Keys (e.g., RS256) so that only your authorization server can issue valid tokens, while resource servers can verify them via published JWKS endpoints.
Strictly Validate Claims, including iss, aud, and exp, and reject tokens missing expected scopes or with stale timestamps.
Keep lifespans short and cryptographically secure, pairing them with refresh tokens or sliding sessions to balance security and usability.
Role-Based vs. Attribute-Based Access Control
Roles group permissions into organized categories, simplifying access management. In contrast, attributes allow policies to adapt dynamically to varying contexts, providing flexibility that enhances both security and user experience.
Feature | RBAC | ABAC |
Model | Predefined roles (admin, user) | Policies based on user, resource, and context attributes |
Granularity | Coarse: one role → permissions | Fine-grained: attribute combinations → decisions |
Use Cases | Stable team hierarchies | Dynamic, multi-tenant SaaS or contextual rules |
Complexity | Easier to implement, harder to scale | More flexible, requires robust policy management |
Mutual TLS (mTLS) for Service–to–Service Authentication
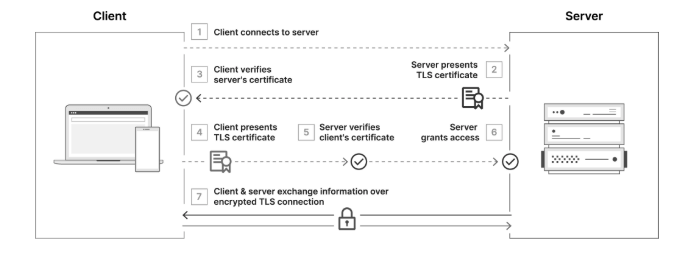
mTLS elevates trust by requiring both peers to present certificates, effectively binding identity to each connection. To deploy at scale:
Automate certificate issuance and rotation via a private PKI or service mesh
Embed service identity in certificate CN/SAN fields
Layer with network policies for granular isolation
Monitor handshake failures to detect compromised or misconfigured services
Employing these advanced patterns guarantees that only authenticated and authorized entities can interact with your APIs and that they can only perform permitted actions according to continuously enforced policies.
Threat Modeling & Risk Assessment for APIs
Effective API security starts with a clear understanding of system vulnerabilities and identifying the threats that pose the greatest risk. Threat modelling and risk assessment offer a structured approach to pinpoint potential attack vectors, whether they involve coding flaws, gaps in authentication, or excessive usage. This process helps prioritize defenses that have the most significant impact.
OWASP API Top 10
The OWASP API Top 10 provides a blueprint of the most critical API vulnerabilities, helping teams focus their risk assessments on the areas attackers exploit most often. A quick overview:
Risk Category | Description |
API1:2023 – Broken Object Level Authorization | APIs often expose endpoints that manage object identifiers, which can lead to numerous Object Level Access Control issues. It is essential to implement object-level authorization checks in every function that interacts with a data source using an identifier provided by the user. |
API2:2023 – Broken Authentication | Authentication mechanisms are often misimplemented, allowing attackers to compromise authentication tokens or exploit flaws in implementation to temporarily or permanently assume other users’ identities. When a system’s ability to accurately identify clients or users is compromised, the overall API security is undermined. |
API3:2023 – Broken Object Property Level Authorization | This category unifies the 2019 concepts of “Excessive Data Exposure” and “Mass Assignment” by addressing their common root cause: inadequate or improper authorization validation at the object property level. This deficiency allows unauthorized parties to access or manipulate sensitive information. |
API4:2023 – Unrestricted Resource Consumption | Satisfying API requests requires resources like network bandwidth, CPU, memory, storage, SMS/phone calls, or biometric validation billed per request. Successful attacks can result in Denial of Service or increased operational costs. |
API5:2023 – Broken Function Level Authorization | Complex access-control policies with overlapping hierarchies, groups, and roles—and an unclear separation between administrative and regular functions—often lead to authorization flaws. Attackers who exploit these flaws can gain unauthorized access to other users' resources or administrative functions. |
API6:2023 – Unrestricted Access to Sensitive Business Flows | APIs that are vulnerable to this risk expose business processes (such as purchasing and commenting) without sufficient controls to prevent automated and excessive usage. This issue often arises from design oversights rather than coding errors, allowing attackers to disrupt business logic or revenue through high-volume automated requests. |
API7:2023 – Server Side Request Forgery (SSRF) | SSRF vulnerabilities arise when an API retrieves a remote resource without validating user-supplied URLs. Attackers can manipulate the application into sending crafted requests to unexpected destinations, potentially bypassing firewalls or VPNs and gaining access to internal systems. |
API8:2023 – Security Misconfiguration | APIs and their supporting systems often have complex configurations for customization. Engineers who overlook these settings or fail to adhere to security best practices may inadvertently leave vulnerabilities open for various attacks, ranging from default credentials to overly permissive CORS policies. |
API9:2023 – Improper Inventory Management | APIs often expose more endpoints than traditional web applications, making accurate and up-to-date documentation and inventory of hosts critical. Without this, deprecated API versions, debug endpoints, or forgotten services can remain exposed and unpatched. |
API10:2023 – Unsafe Consumption of APIs | Developers often trust data from third-party APIs more than user input, applying weaker security standards. Attackers exploit these integrated services, rather than the target API itself, to inject malicious payloads or gain unauthorized access through less-protected chains of trust. |
Choosing & Applying a Threat-Modeling Framework
Structured threat modeling ensures you cover all angles, not just the low-hanging fruit. Selecting the right framework helps you reason about threats systematically:
Framework | Focus | Output |
STRIDE | Spoofing, Tampering, Repudiation | Threat enumeration per category |
DREAD | Damage, Reproducibility, Exploitability | Quantified risk scores |
Begin by mapping API workflows, then apply STRIDE to identify potential threats. Use DREAD scoring to prioritize threats based on business impact and ease of exploitation.
API Fuzzing, Penetration Testing & Automated Scans
Once threats are cataloged, test for them through:
Fuzzing: Send random or mutated inputs to uncover parsing errors.
Penetration Testing: Manual or red-team exercises targeting logic and business-layer flaws.
Automated Scanners: Integrate SAST/DAST tools to catch known vulnerability patterns early.
Prioritizing & Mitigating High-Impact Threats
Not all risks warrant equal effort. Focus first on vulnerabilities that:
Expose sensitive data (e.g., broken object authorization)
Enable easy privilege escalation (e.g., misconfigured roles)
Can be automated at scale (e.g., injection, DoS)
Mitigation tactics consist of schema validation, WAF rules, strict rate limiting, and regular key rotation. By integrating threat modeling with thorough testing and clear risk prioritization, you ensure your API defenses evolve alongside new attack techniques.
Runtime Protection & Monitoring
During runtime, APIs face a constant flow of both legitimate and malicious traffic. Effective protection and monitoring ensure that policy enforcement, threat mitigation, and anomaly detection occur in real time—before attackers can exploit vulnerabilities or overload your services.
API Gateways vs. Service Meshes
While both API gateways and service meshes centralize control, they serve different scopes and use cases. Choose the right layer for policy enforcement to balance performance, flexibility, and operational complexity:
Capability | API Gateway | Service Mesh |
Scope | North–south traffic (client ↔ services) | East–west traffic (service ↔ service) |
Policy Types | Authentication, authorization, routing | Mutual TLS, circuit breaking, retries |
Deployment | Single entry point | Sidecar proxies alongside each service |
Latency Impact | Minimal for light policies | Slightly higher due to sidecar hops |
Use Case | Public APIs, B2B/B2C gateways | Microservices within a cluster |
Web Application Firewalls (WAFs) Tailored for APIs
A WAF specialized for APIs inspects JSON/XML payloads and HTTP methods to block common exploits:
Schema Validation: Reject requests deviating from defined JSON schemas
Rate-Based Rules: Automatically block IPs that exceed thresholds
Behavioral Signatures: Detect SQL/NoSQL injection, XML external entities, GraphQL introspection abuse
IP Reputation Feeds: Preemptively block known malicious sources
Anomaly Detection & Behavioral Analytics
Beyond static rules, behavioral analytics learns normal API usage patterns and flags deviations:
Unusual Spike Detection: Alerts when traffic deviates from historic baselines
Payload Profiling: Identifies malformed or suspicious request bodies
User Behaviour Modelling: Spots credential stuffing or lateral movement across endpoints
Automated Response: Throttle or quarantine anomalous clients pending review
Rate-Limiting, Quotas & Dynamic Throttling
Throttling controls protect against both malicious floods and accidental overload:
Fixed Quotas: Enforce hard caps per API key or user
Burstable Limits: Allow short traffic spikes while preserving long-term caps
Dynamic Throttling: Adjust limits based on real-time server load and latency
Graceful Degradation: Serve cached or reduced-functionality responses under heavy load
By integrating policy enforcement at the right layer with adaptive runtime defenses and ongoing monitoring, you can detect and mitigate attacks in real-time, ensuring your APIs remain reliable and secure.
DevSecOps & Secure SDLC Integration
Incorporating security at every stage of development helps catch vulnerabilities early, allowing fixes to seamlessly flow into production. By considering security a core element instead of an afterthought, you can lower risks, speed up releases, and foster confidence across teams.
Shifting Security Left: Integrating SAST & DAST into CI/CD
Early detection of flaws prevents costly late-stage fixes.
SAST (Static Analysis): Scans source code for vulnerabilities before compilation
DAST (Dynamic Analysis): Tests running applications and APIs for runtime issues
Integration Steps:
Add SAST to pull-request gates (fail builds on high-severity findings)
Run DAST against deployed test environments on every merge
Automate report generation and ticket creation for triage
SAST | DAST | |
When | Pre-build | Post-deployment |
What | Code patterns, secrets | HTTP endpoints, business logic |
Benefits | Early feedback | Real-world attack simulation |
Limitations | False positives | Requires stable test environment |
Security as Code: Policy-Driven Configurations
Codifying security ensures consistency and version control:
Use Open Policy Agent (OPA): Define authorization, ingress, and resource quotas as code
Embed Policies in Repos: Store policies alongside application code for change tracking
Enforce via CI: Validate policy syntax and simulate policy impact before merge
Automated Dependency & Supply-Chain Checks
Third-party libraries often introduce hidden risks—automate their vetting:
Dependency Scanners: Tools like Dependabot or Snyk flag outdated or vulnerable packages
Software Bill of Materials (SBOM): Maintain an SBOM to trace every component and its licenses
Container/Image Scanning: Integrate tools (Clair, Trivy) into your build pipeline to block unsafe images
Continuous Compliance & Audit Trails
Ongoing validation and traceability keep you aligned with regulations and internal standards:
Automated Compliance Checks: Embed CIS Benchmarks or NIST controls into pipeline stages
Immutable Logs: Ship build, test, and deployment logs to a centralized system (e.g., ELK, Splunk)
Alerting & Reporting: Generate real-time dashboards and periodic compliance reports for stakeholders
By integrating these DevSecOps practices, security becomes an enabler—accelerating delivery while maintaining a robust, auditable defense posture.
Conclusion
As APIs play a crucial role in modern applications, it is essential to enhance your security measures beyond basic protocols. In this article, we explored various advanced techniques designed to strengthen your APIs at every level. These techniques include identity verification, continuous monitoring, and the integration of DevSecOps.
Recap of Key Advanced Strategies
Advanced Authentication & Authorization: OAuth 2.0 with PKCE, JWT best practices, RBAC/ABAC models, and mTLS for service-to-service trust.
Threat Modeling & Risk Assessment: OWASP API Top 10 deep dives, STRIDE/DREAD frameworks, fuzzing, pen testing, and automated scans to prioritize critical vulnerabilities.
Runtime Protection & Monitoring: Policy enforcement at gateways vs. meshes, API-tailored WAFs, behavioral analytics, and adaptive throttling to detect and stop attacks in real time.
DevSecOps & Secure SDLC: “Shift left” with SAST/DAST in CI/CD, policy-as-code (OPA), automated supply-chain checks, and continuous compliance auditing.
Business & Technical Benefits of “Beyond Basics” API Security
Reduced Risk & Liability: Proactively block exploits, data leaks, and DDoS downtime.
Improved Reliability: Maintain consistent performance and uptime under load or attack.
Enhanced Customer Trust: Demonstrate strong protections for sensitive data and transactions.
Regulatory Alignment: Meet compliance mandates (e.g., GDPR, PCI DSS) with auditable logs and controls.
Operational Efficiency: Lower incident response times (MTTD/MTTR) and reduce manual firefighting.
To build your API security roadmap, start by taking stock of your APIs. Check your current security measures and identify potential threats. Make sure your risk assessments align with the potential business impact to choose the most effective defenses.
Implement one advanced security measure, like mutual TLS (mTLS) or security checks in your workflow. Collect data on its effectiveness and make improvements as needed.
Incorporate successful strategies into your systems, such as gateways and policy tools. Keep an eye on important security metrics, carry out regular practice drills, and update your roadmap to address new threats.
Akava would love to help your organization adapt, evolve and innovate your modernization initiatives. If you’re looking to discuss, strategize or implement any of these processes, reach out to [email protected] and reference this post.