Table of Contents
Actionable insights on applying Zero Trust principles to CI/CD pipelines to strengthen security without slowing delivery.
Modern software delivery has quietly become one of the most attractive attack surfaces in the enterprise. Over the last few years, high-profile supply chain incidents involving SolarWinds, Codecov, and CircleCI have made one thing clear: attackers no longer need to breach production systems directly if they can compromise the pipeline that builds and deploys them.
CI/CD pipelines now sit at the intersection of source code, secrets, cloud infrastructure, and deployment automation. They routinely hold privileged credentials, sign artifacts, and push changes straight into production environments. A single misconfigured runner, leaked token, or over-permissioned workflow can provide attackers with a level of access that would be difficult to obtain elsewhere. As organizations accelerate delivery and automate more aggressively, pipelines have become both indispensable and dangerously powerful.
Traditional security models struggle in this environment. Implicit trust between tools, long-lived credentials, and broad permissions were once considered acceptable tradeoffs for speed. Today, those assumptions no longer hold. The threat landscape has evolved, and so must the security model that protects software delivery.
This is where Zero Trust becomes more than a buzzword. Applied to CI/CD, Zero Trust means assuming breach by default, minimizing implicit trust, and continuously verifying every action, identity, and interaction whether it originates from a developer, a build job, or an automation script.
Embedding Zero Trust into CI/CD pipelines is no longer optional. The real-world failures of modern cloud pipelines offer hard-earned lessons and a practical roadmap for building delivery systems that are fast, automated, and resilient by design.
Understanding Zero Trust in the Context of CI/CD
Zero Trust is often reduced to a slogan, but in practice it represents a fundamental shift in how systems establish trust. At its core, Zero Trust rejects implicit assumptions and replaces them with three principles: strong identity, least privilege, and continuous verification. No user, service, or workload is trusted by default every action must be authenticated, authorized, and validated in real time.
Applied to CI/CD, this philosophy becomes especially critical. Pipelines are not just build tools anymore; they are highly privileged automation systems. They pull source code, fetch dependencies, inject secrets, sign artifacts, and deploy directly to production. They also combine human identities (developers triggering builds) with machine identities (runners, containers, orchestrators), creating a dense web of trust relationships that traditional security models were never designed to handle.
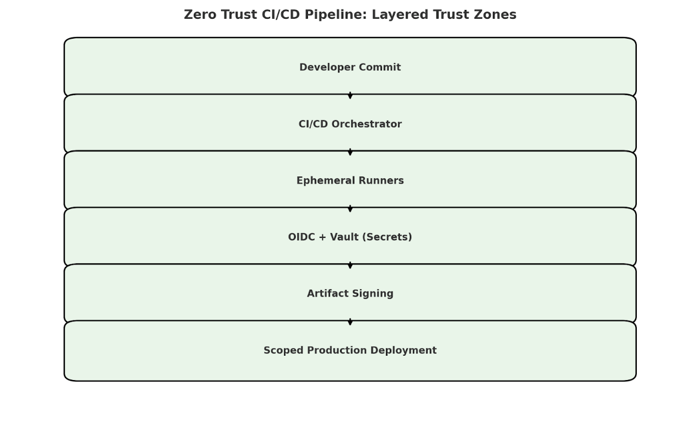
Traditional perimeter-based security assumes that anything inside the network is safe. In CI/CD environments, that assumption collapses immediately. Build runners are ephemeral, dependencies are external, and pipelines routinely execute untrusted code from pull requests. Once an attacker gains a foothold via a compromised dependency, misconfigured runner, or leaked token they can move laterally with alarming speed.
Zero Trust addresses this by treating every pipeline component as potentially compromised. Runners execute in fully isolated environments, provisioned on demand, with no inherited state. Outbound network access is denied by default. Static credentials and shared tokens are replaced with short-lived identity tokens, typically issued via OIDC and scoped to a single job. These identities are traceable to a specific git SHA and build ID, and they expire immediately after execution.
The result is a dramatically reduced blast radius. Even if malicious code is injected into a job, the window of opportunity is measured in minutes, not days—and the privileges available are intentionally minimal. In CI/CD, Zero Trust is not theoretical security; it is operational containment at machine speed.
Threat Landscape for Modern Pipelines
CI/CD pipelines have become one of the most attractive targets in modern cloud environments. They sit at the crossroads of source code, secrets, and production access making them an ideal entry point for attackers looking to scale their impact quickly. Understanding the most common attack vectors is essential to applying Zero Trust effectively.
Common Attack Vectors
Several threat patterns consistently emerge across compromised pipelines:
Compromised credentials: Leaked API tokens, long-lived cloud credentials, or hardcoded secrets in build scripts remain one of the fastest ways into a pipeline.
Dependency poisoning: Malicious code injected into third-party dependencies can execute automatically during builds, often with elevated privileges.
Misconfigured secrets management: Over-permissioned runners or shared secret stores allow lateral movement once a single job is compromised.
Insider threats: Developers or contractors with excessive permissions can unintentionally or deliberately introduce vulnerabilities into pipelines.
What makes these attacks especially dangerous is that they often blend in with normal automation, evading traditional detection mechanisms.
Real-World Examples
The SolarWinds attack demonstrated how a compromised build process can propagate malicious code to thousands of downstream customers. Similarly, the Codecov breach demonstrated that a single leaked credential in a CI script enabled attackers to exfiltrate sensitive environment variables across numerous organisations.
In both cases, CI/CD pipelines were not secondary victims; they were the primary attack surface. Once compromised, they provided trusted distribution channels that bypassed many downstream security controls.
Risks Unique to Cloud-Native Environments
Cloud-native pipelines introduce additional complexity. Ephemeral infrastructure, while beneficial for isolation, makes forensic analysis more difficult if logs and artefacts aren’t captured centrally. Multi-cloud and SaaS dependencies expand the trust boundary far beyond a single provider, increasing exposure to third-party failures or misconfigurations.
Organizations adopting Zero Trust often encounter challenges such as configuration complexity, slower deployments due to added controls, and tool sprawl. Successful teams address this incrementally, starting with identity-first measures like OIDC, applying security policies in stages, and leveraging native CI/CD security features before introducing new tools.
Large-scale adopters like Netflix and Capital One have shown that securing pipelines with scoped access, artifact signing, and short-lived credentials significantly reduces blast radius without sacrificing delivery speed.
Zero Trust Principles Applied to CI/CD
Zero Trust is not a single control or tool it’s a set of reinforcing principles that redefine how trust is established and maintained. In CI/CD pipelines, these principles govern how identities are verified, how access is constrained, and how systems behave under the assumption that compromise is possible at any point. The objective is not to slow delivery, but to reduce blast radius while preserving speed.
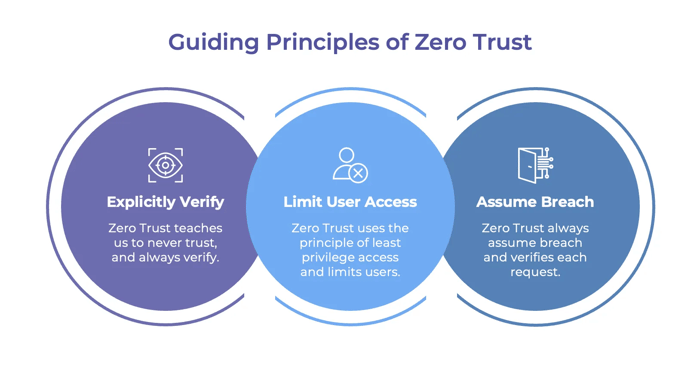
Explicitly Verify
Zero Trust begins with never trusting by default. Every identity and action in the pipeline must be explicitly verified, regardless of whether it originates from a developer, an automation job, or an internal service.
In CI/CD, this means treating everything as an identity: developers, CI jobs, runners, bots, and deployment workflows. Static credentials and shared secrets are replaced with federated, short-lived identities.
A common implementation pattern is workload identity federation using OIDC. CI systems authenticate to cloud providers by presenting an OIDC token that proves the identity of the workflow. That token is exchanged for temporary credentials scoped to a specific job and execution context. No secrets are stored, and no credentials persist beyond the lifetime of the job.
Every action is traceable to a specific git SHA, build ID, and workflow—making verification continuous, auditable, and non-reusable by design.
Limit User Access
Verification alone is not enough. Zero Trust also requires strict limitation of access through least-privilege enforcement.
In CI/CD pipelines, this translates to fine-grained permissions such as:
Repository access scoped by branch, environment, and workflow
Build jobs allowed to compile and test but not deploy
Deployment jobs permitted to release artifacts but not modify source code
Separation of duties is critical. A compromised build job should never inherit production access simply because it succeeded. By enforcing tight, role-specific permissions, organizations ensure that no single pipeline stage can escalate privileges unchecked.
Access is granted only when needed, for only what is needed, and for the shortest possible duration.
Assume Breach
The final principle acknowledges reality: systems will fail, and attackers will get in. Zero Trust pipelines are designed so that failure at one layer does not compromise the entire system.
This is where defense-in-depth becomes operational. Artifacts are signed after build and verified before deployment, ensuring only trusted outputs are promoted. Provenance frameworks such as SLSA and in-toto establish a verifiable chain of custody from source to runtime.
Runners execute in isolated, ephemeral environments with no inherited state. Network access is restricted by default. Runtime monitoring tools detect anomalous behavior during execution, providing real-time signals if something deviates from expected behavior.
By assuming breach, CI/CD pipelines shift from implicit trust engines to containment-first systems.
Applied together, these three principles, explicit verification, limited access, and breach assumption, transform CI/CD pipelines into continuously verified delivery systems: secure by default, auditable by design, and resilient against modern supply chain threats.
Implementation Blueprint
Embedding Zero Trust into CI/CD pipelines doesn’t require a ground-up rebuild. The most successful teams treat it as an incremental engineering program, not a one-time security project. The goal is to reduce risk steadily while preserving delivery velocity.
Assess Pipeline Maturity
Begin by understanding where your pipelines stand today. Inventory how builds are triggered, where secrets live, which credentials are long-lived, and which jobs have access to production environments. Most teams discover that trust has accumulated implicitly over time. This assessment establishes a baseline and helps prioritize changes that deliver the highest risk reduction early.
Define Trust Boundaries and Critical Assets
Next, identify what must be protected most. Source code repositories, signing keys, container registries, cloud credentials, and deployment permissions are typically high-value assets. Clearly defining trust boundaries between developers and pipelines, pipelines and cloud providers, builds and deployments makes it easier to apply controls deliberately rather than reactively.
Integrate Zero Trust Incrementally
Zero Trust works best when introduced in layers:
Identity and Secrets First: Replace static credentials with short-lived, federated identities. CI jobs should authenticate dynamically using OIDC and retrieve secrets only when needed, for the shortest possible duration.
Artifact Integrity: Once identities are secured, ensure that what you build is what you deploy. Sign artifacts, generate provenance metadata, and verify integrity before promotion across environments.
Deployment Controls: Finally, scope deployment permissions tightly. Enforce separation between build and deploy stages, require policy checks before production releases, and ensure that deployments are traceable to verified artifacts and approved workflows.
Each layer compounds the effectiveness of the previous one.
Tooling Ecosystem
Modern tooling makes this approach achievable without excessive overhead. CI platforms like GitHub Actions or GitLab provide native OIDC integration. Policy enforcement can be implemented with Open Policy Agent and Conftest. Secrets management is commonly handled by HashiCorp Vault. Artifact signing and verification are enabled by Sigstore tools like Cosign, while SLSA frameworks provide structured supply chain guarantees.
Measuring Success
Zero Trust adoption should be measurable. Useful KPIs include reduction in long-lived credentials, percentage of pipelines using federated identity, artifact verification coverage, and mean time to revoke access after pipeline completion. Over time, these metrics shift security conversations from fear-based controls to observable, enforceable outcomes.
A disciplined, incremental approach turns Zero Trust from an abstract ideal into an operational reality for CI/CD.
Conclusion
Zero Trust isn’t just a checklist or a tool you can set up and forget it’s a journey of continuous improvement that grows along with your systems, teams, and the ever-changing threat landscape. This is especially important in the world of CI/CD, where our pipelines aren't just automated workflows anymore; they have become dynamic environments that play a crucial role in deploying code to production and managing sensitive infrastructure.
When we apply Zero Trust principles to our CI/CD processes, we’re reinforcing one of the traditionally vulnerable and often overlooked areas of software development. By actively verifying every user’s identity, limiting access based on necessity, and operating under the assumption that breaches can happen, organizations can significantly minimize potential damage while maintaining fast delivery. This shifts our approach from relying on implicit trust to a system of ongoing validation and containment.
The main takeaway here is simple: security and speed don’t have to be at odds with each other. When we weave Zero Trust principles into the fabric of our pipelines, we can achieve a balance that allows teams to deliver quickly and confidently, even as the supply chain landscape grows more challenging and complex.
Akava would love to help your organization adapt, evolve and innovate your modernization initiatives. If you’re looking to discuss, strategize or implement any of these processes, reach out to [email protected] and reference this post.